Cryptography | Free Full-Text | Automated Classical Cipher Emulation Attacks via Unified Unsupervised Generative Adversarial Networks
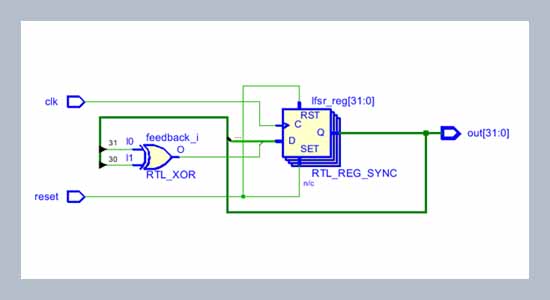
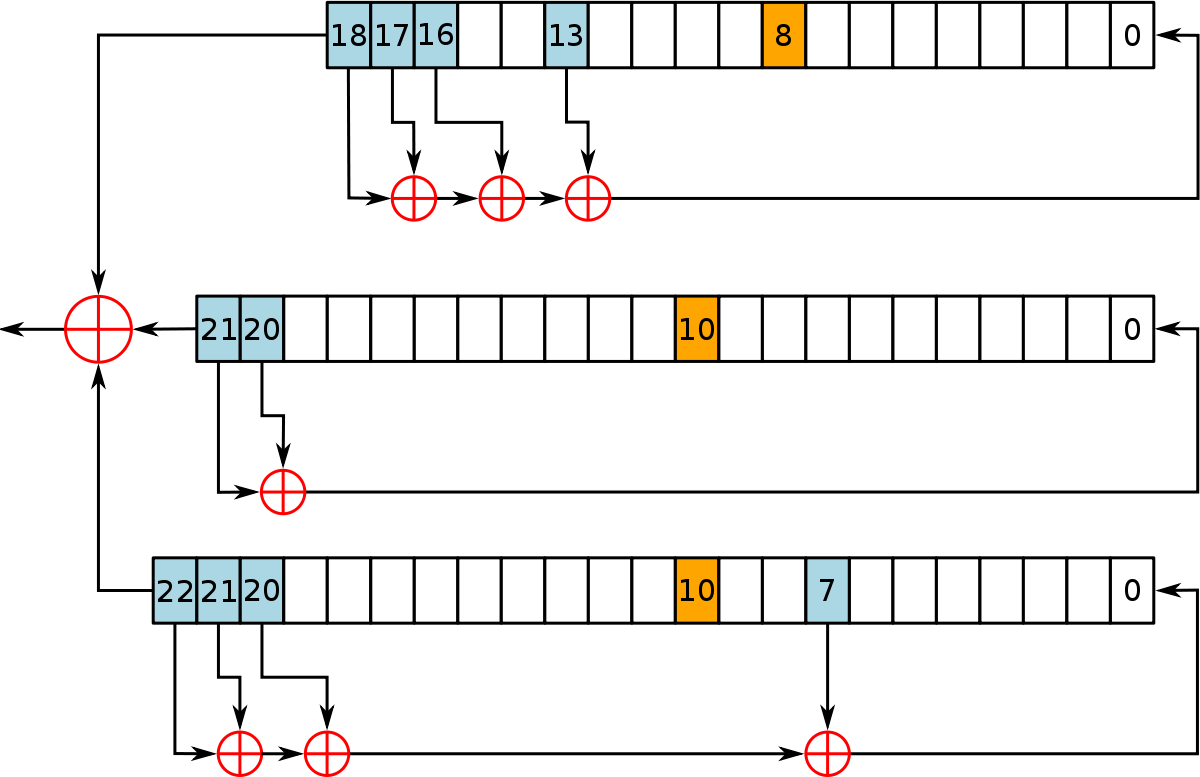
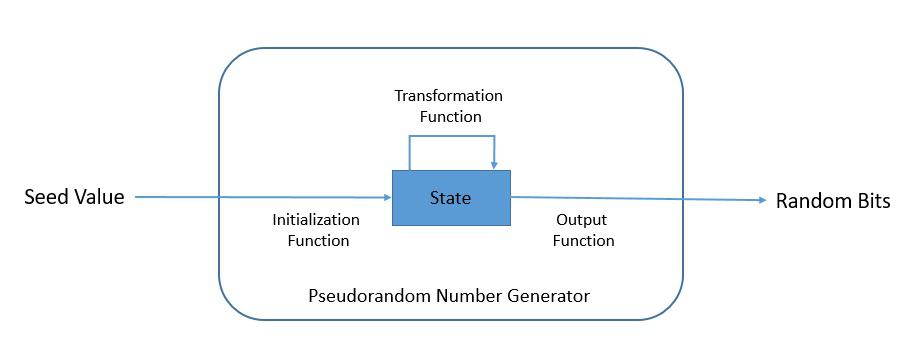
FPGA implementation of random number generator using LFSR and scrambling algorithm for lightweight cryptography

Distributing a Private Key Generator in Ad hoc Networks: Authority Distribution Using Threshold Cryptography: Stenberg, Eystein Måløy: 9783838387710: Amazon.com: Books

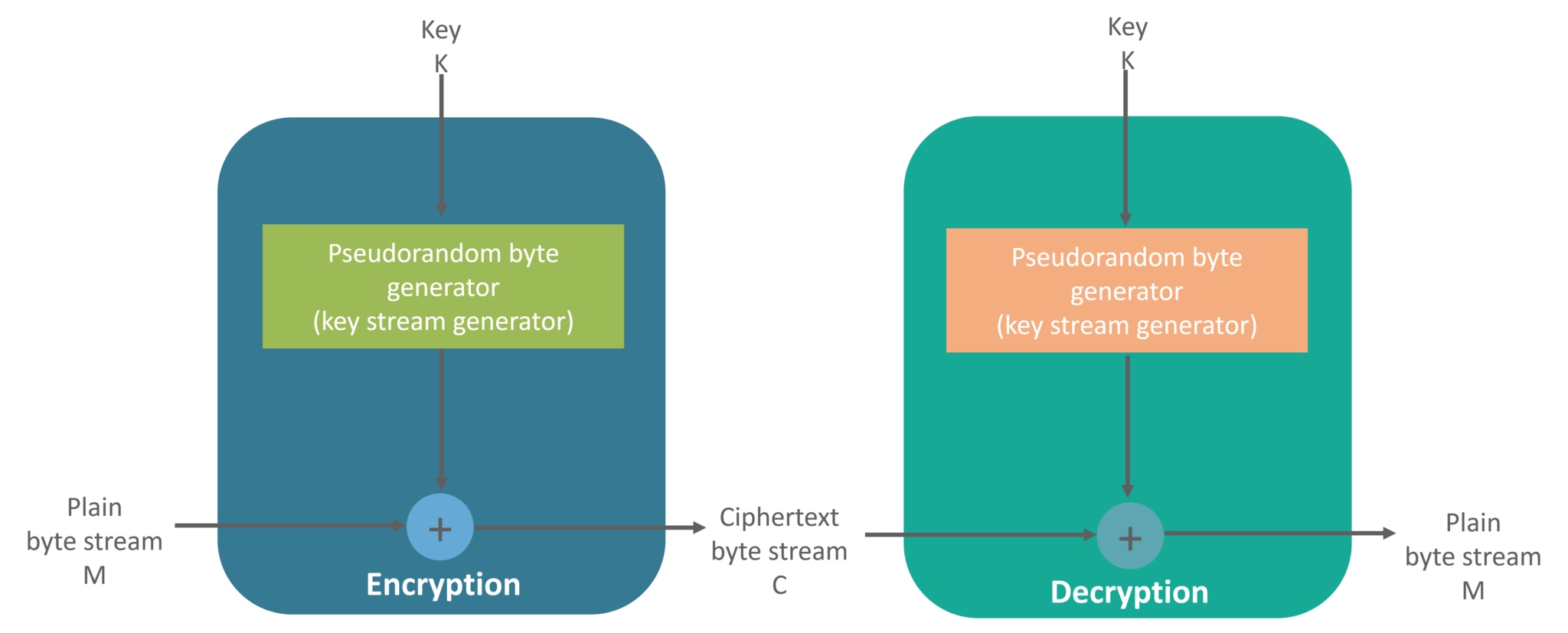
why XOR is recommended/Used in every paper I read for encryption and decryption stream cipher? - Cryptography Stack Exchange
Automated cryptocode generator is helping secure the web | MIT News | Massachusetts Institute of Technology