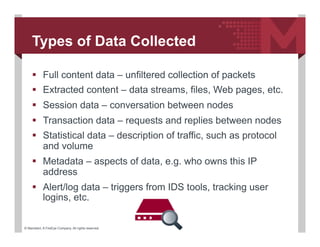
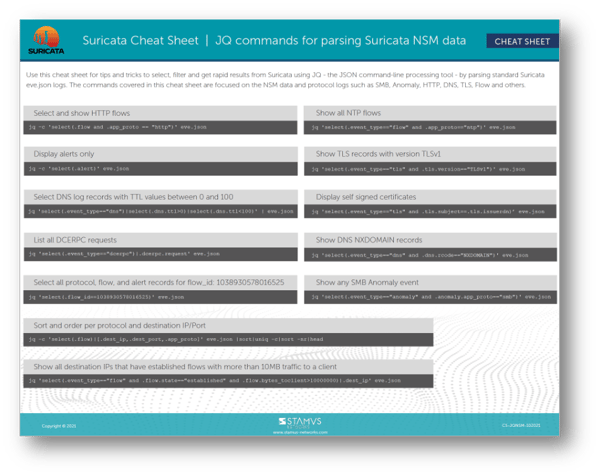
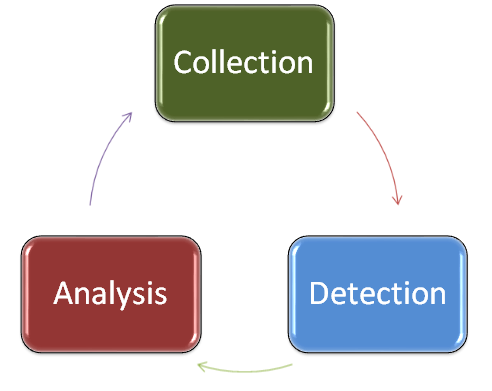
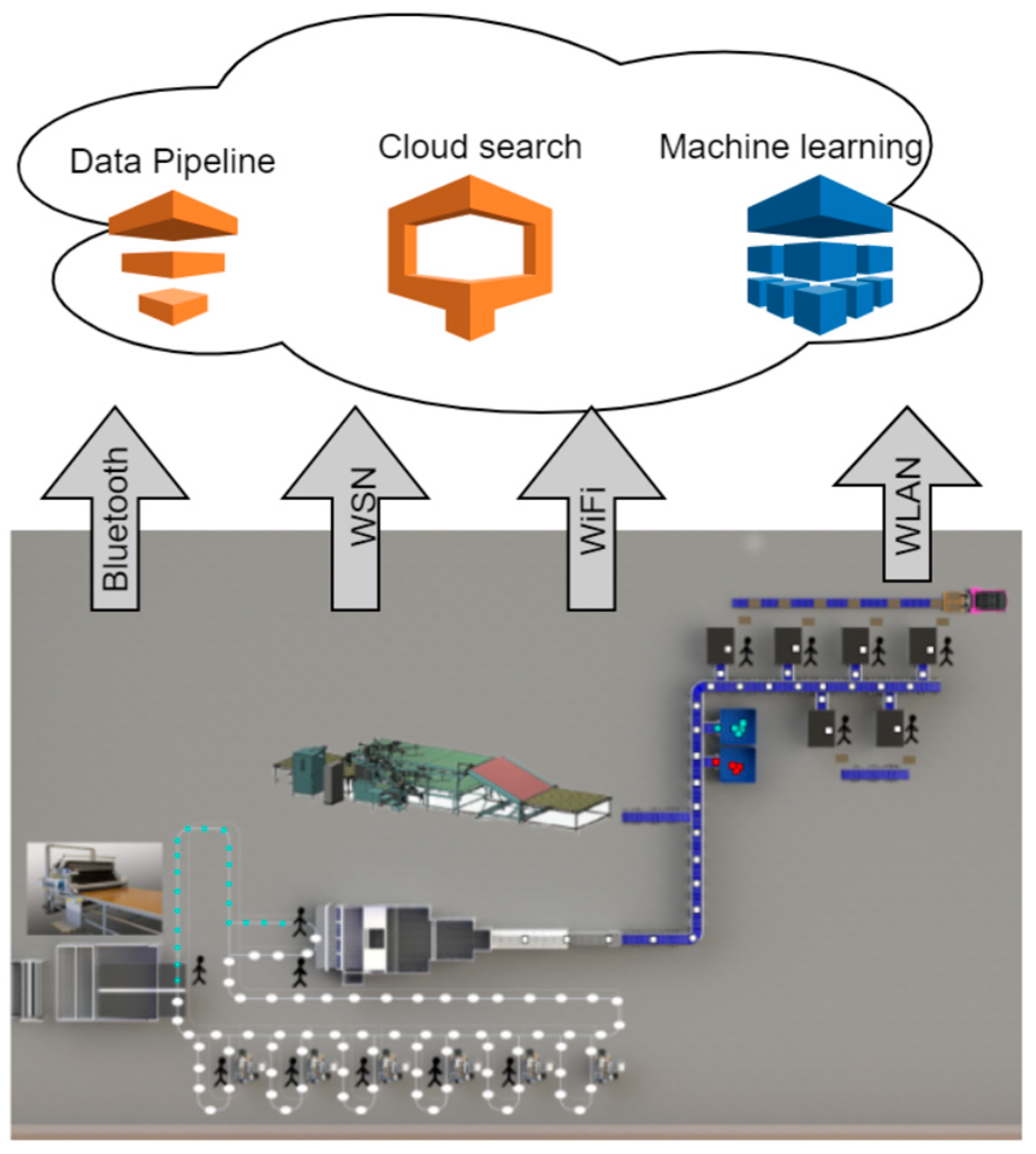
PDF) Anomaly Detection Mechanism based on Common NSM Data Objects for Advanced Metering Infrastructure | ACSIJ Journal - Academia.edu

Anomaly Detection Mechanism based on Common NSM Data Objects for Advanced Metering Infrastructure | Semantic Scholar

LFN Webinar: Building CNFs with FD.io VPP and NSM + VPP traceability in cloud-native deployments - YouTube

Anomaly Detection Mechanism based on Common NSM Data Objects for Advanced Metering Infrastructure | Semantic Scholar