Single Sign-On(SSO) -SAML Authentication Explained | by Prakhar Jain | Connected Lab TechBlog | Medium

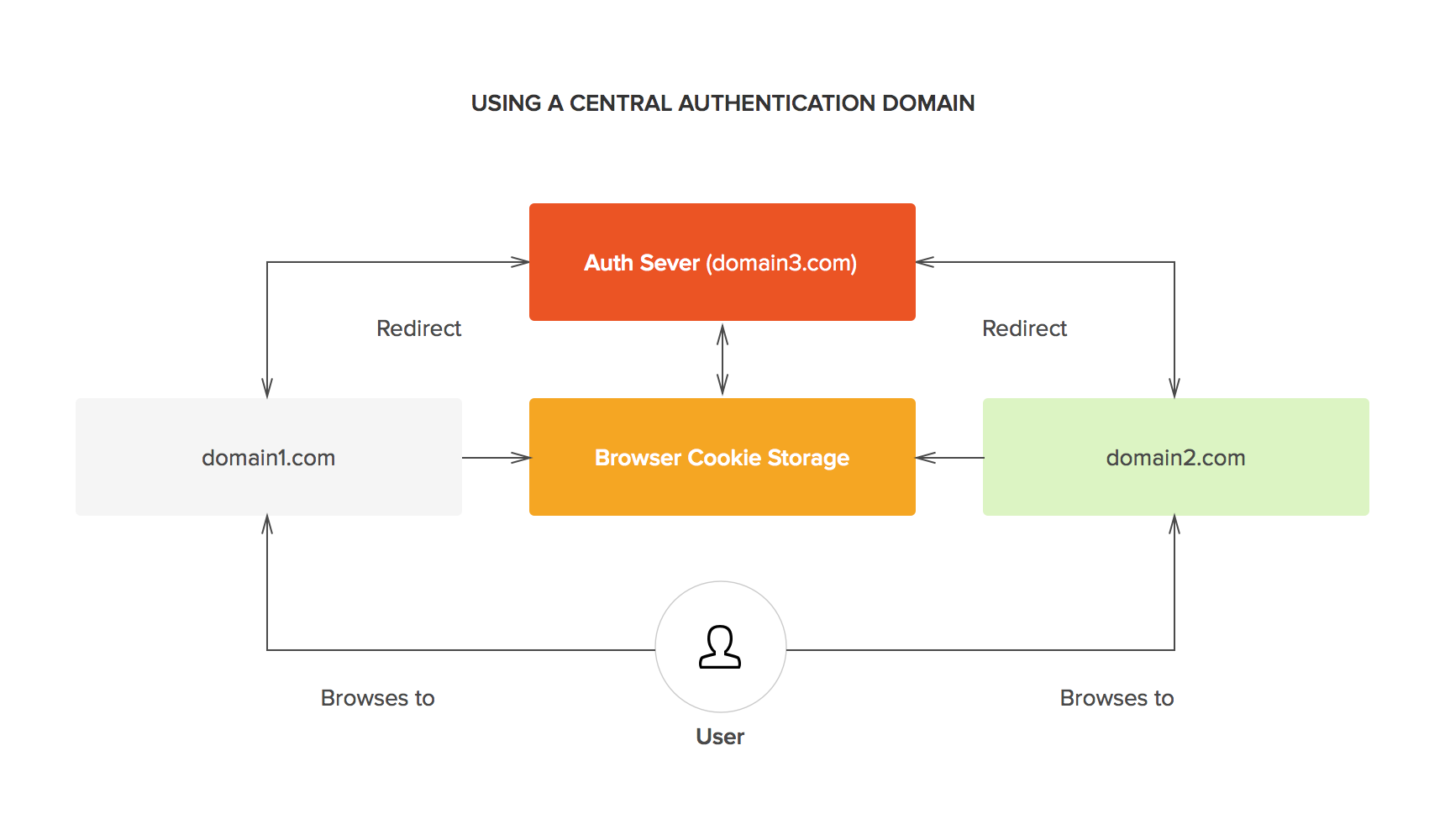
Single Sign-On(SSO) -SAML Authentication Explained | by Prakhar Jain | Connected Lab TechBlog | Medium

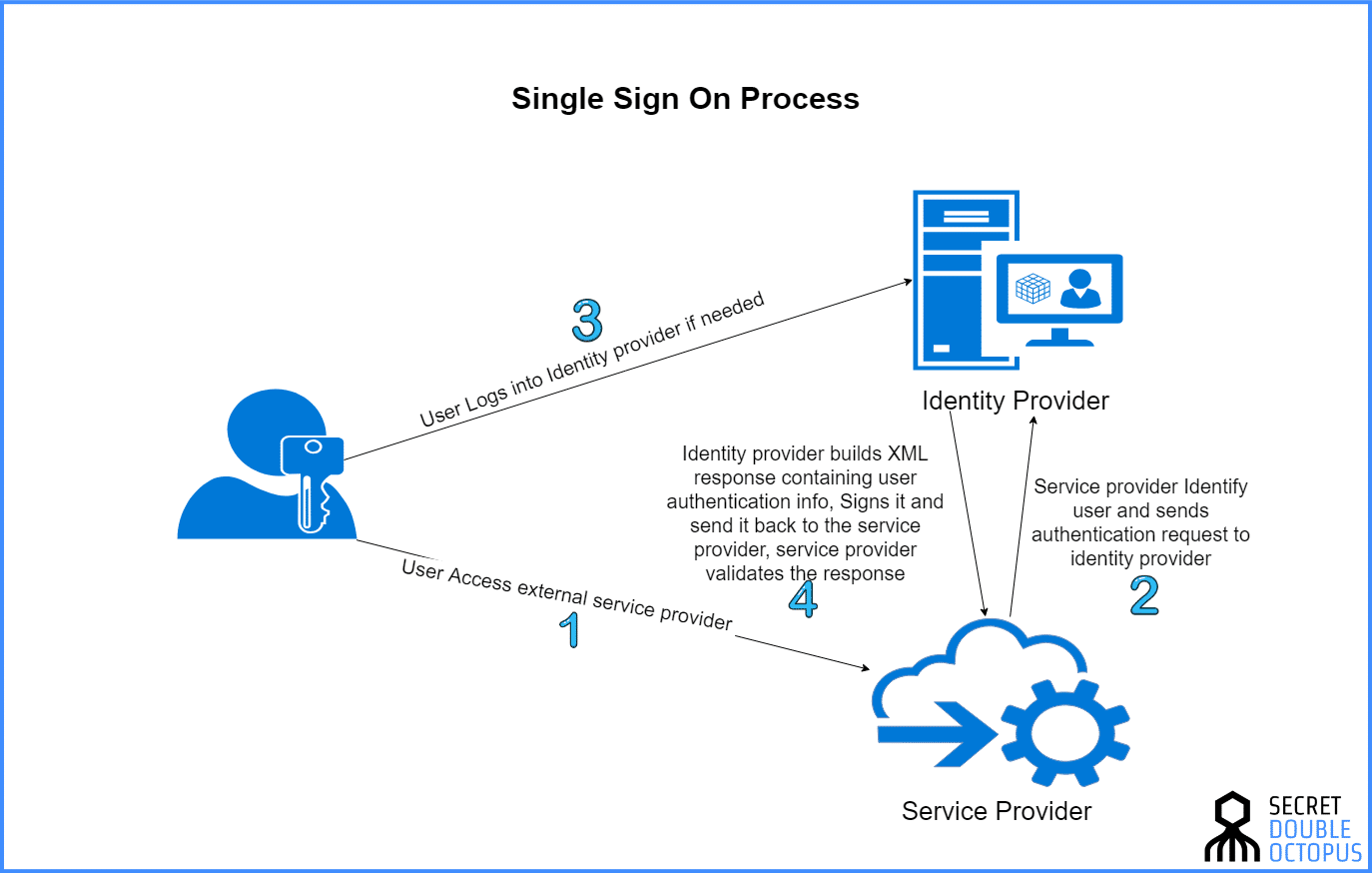
SAML web-based authentication for Security (Single Sign-On SSO) | by Kubernetes Advocate | AVM Consulting Blog | Medium

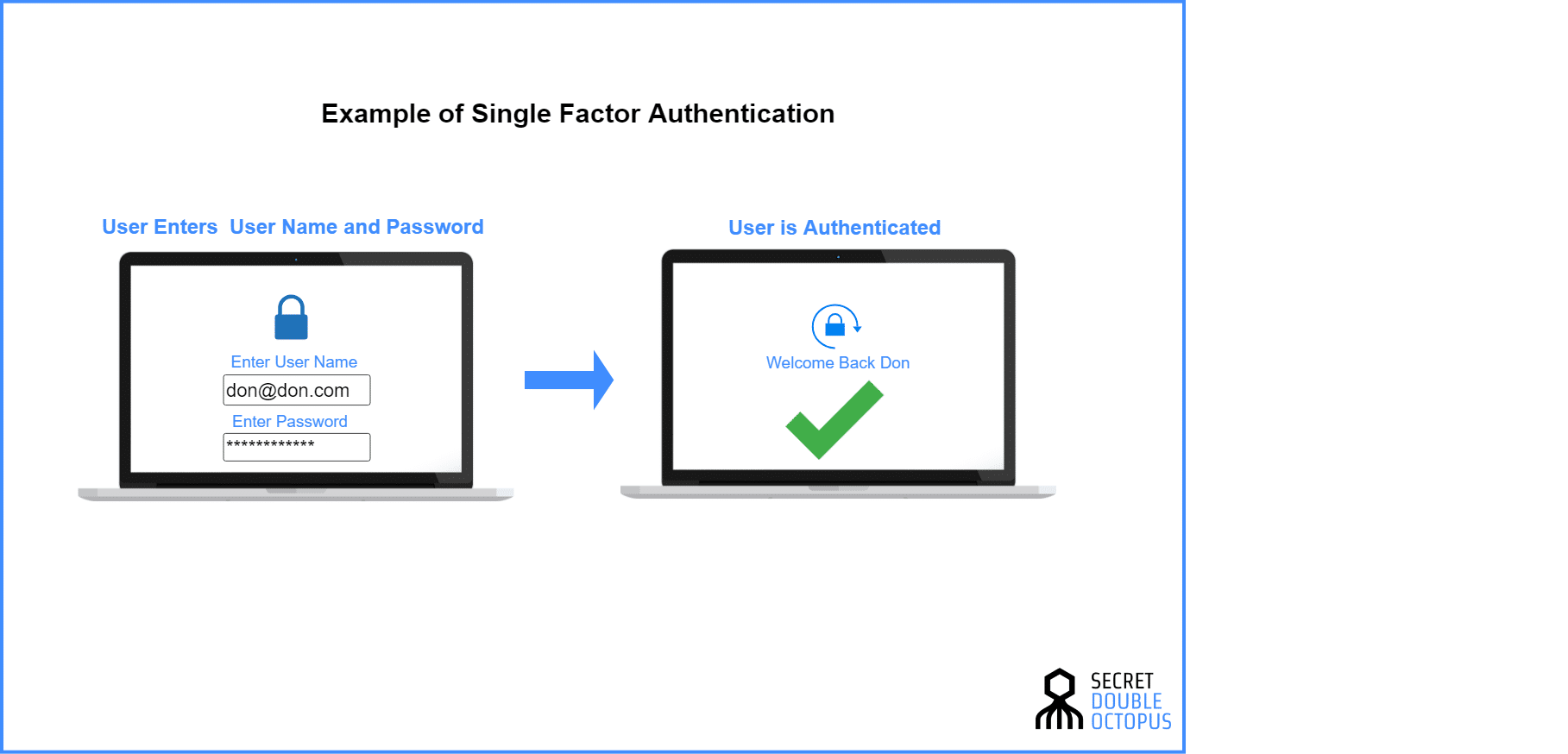
Why Single Factor Authentication Isn't Enough to Protect Your Organization's Network - The Driz Group