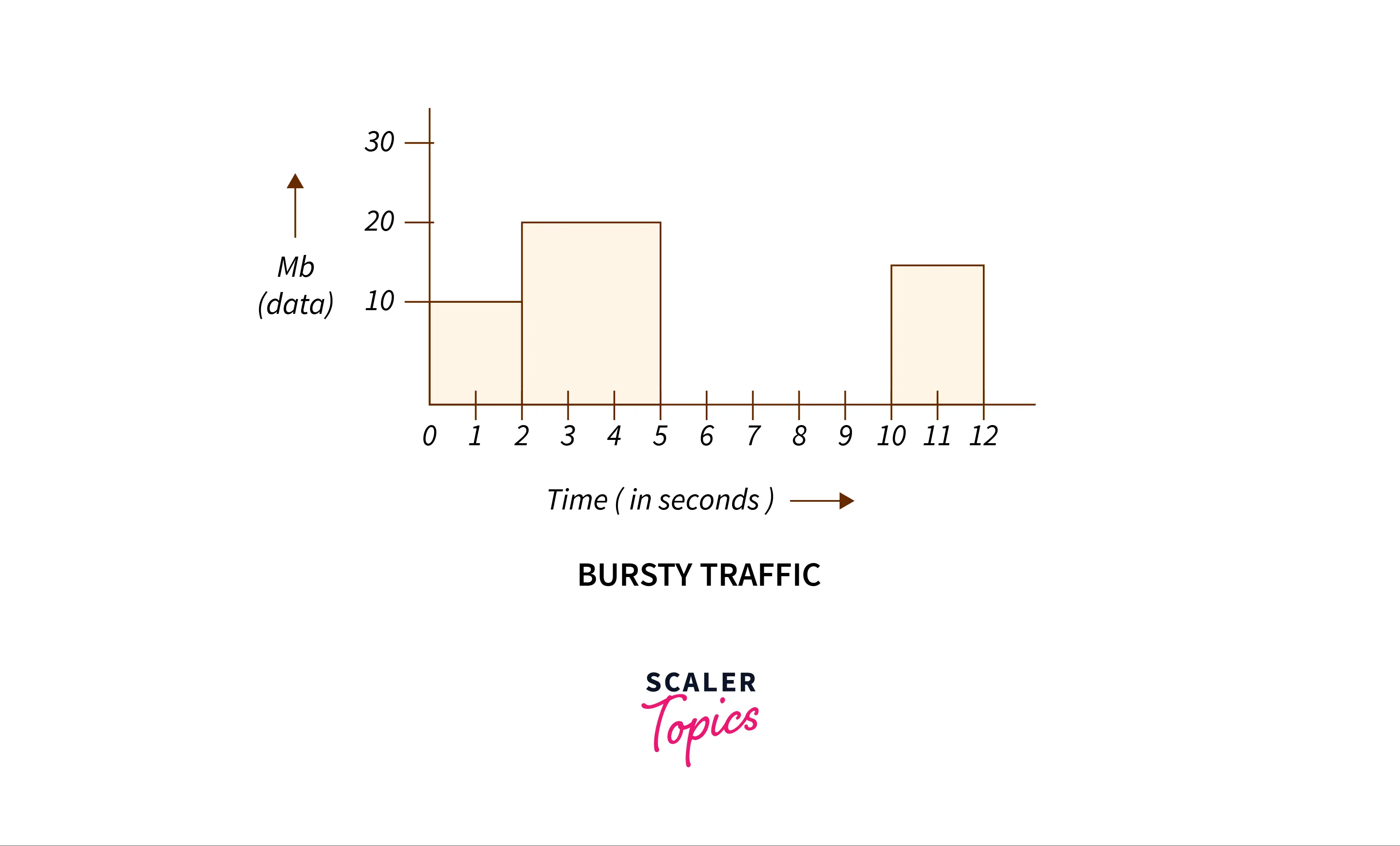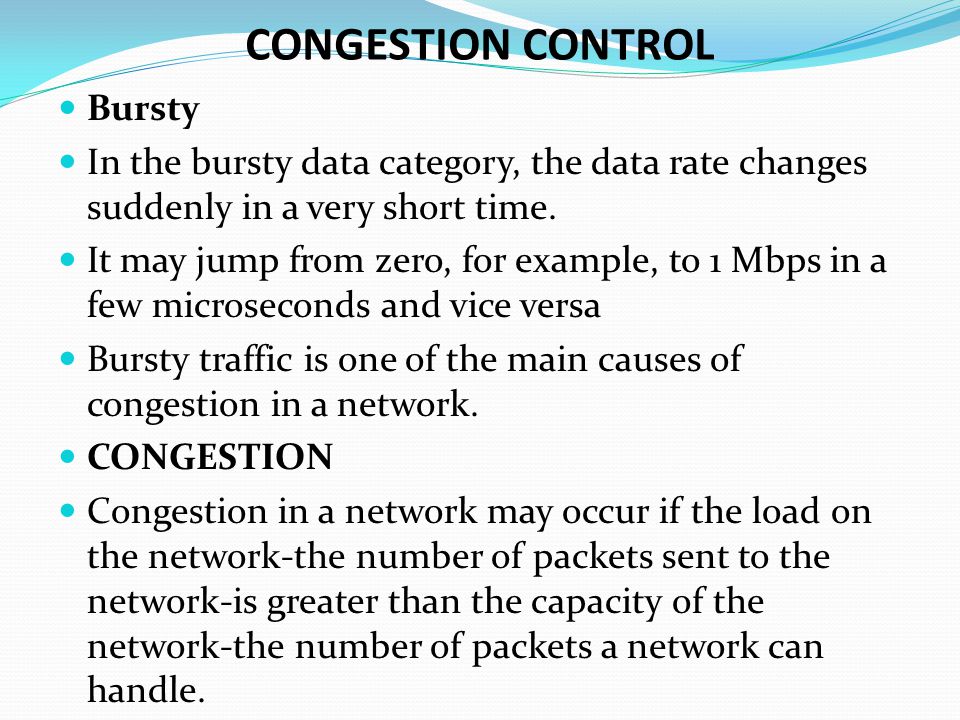
NETWORK LAYER. CONGESTION CONTROL In congestion control we try to avoid traffic congestion. Traffic Descriptor Traffic descriptors are qualitative values. - ppt download

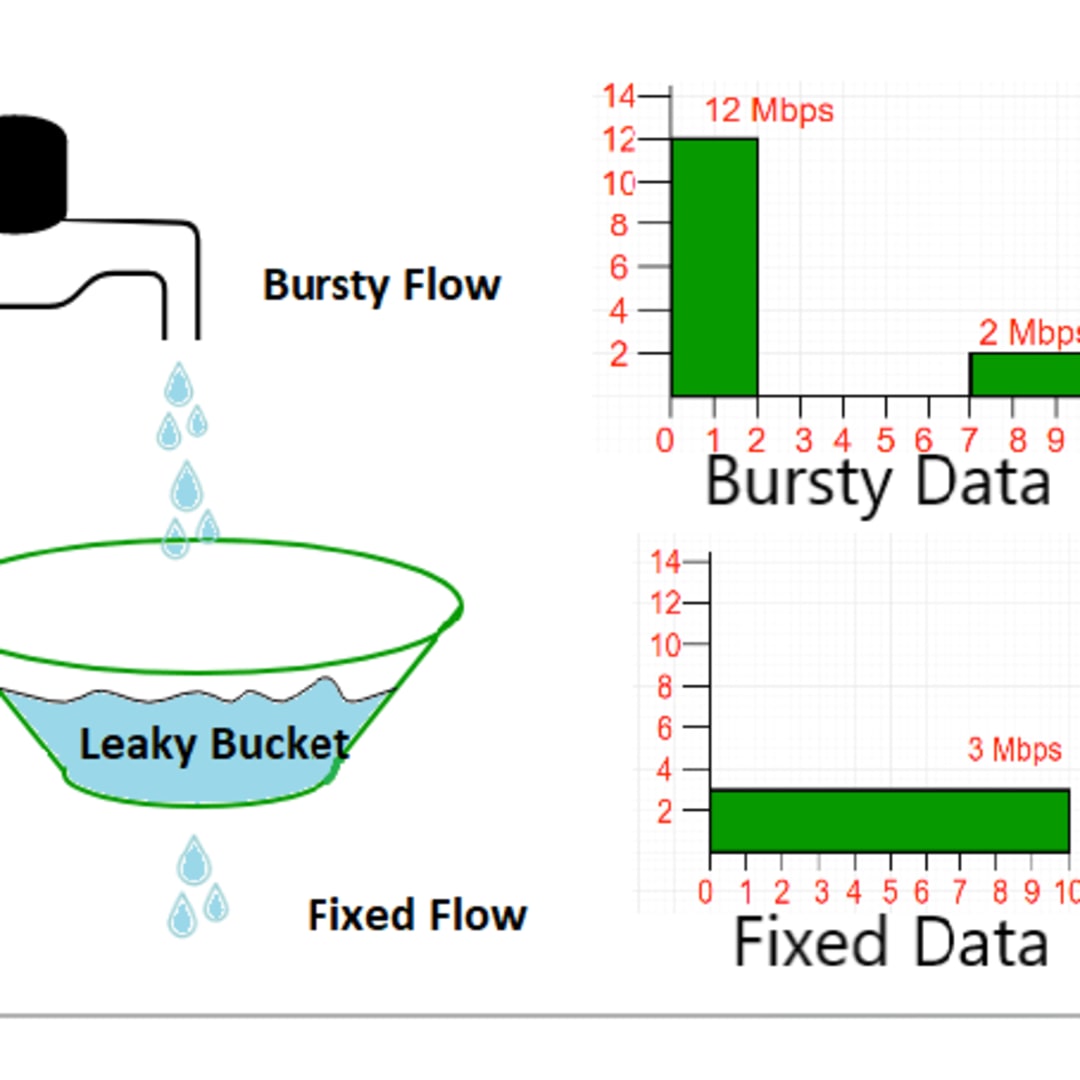
Congestion Control in Computer Network -Leaky Bucket Algorithm/Safad Ismail,Asst.Professor,CASM,IHRD - YouTube
Adaptive Monitoring of Bursty Data Streams Brian Babcock, Shivnath Babu, Mayur Datar, and Rajeev Motwani. - ppt download

Adaptive Frequency Counting over Bursty Data Streams Bill Lin, Wai-Shing Ho, Ben Kao and Chun-Kit Chui Form CIDM ppt download

PDF) Bandwidth allocation and selective discarding for variable bit rate video and bursty data calls in ATM networks | Maurizio Decina - Academia.edu

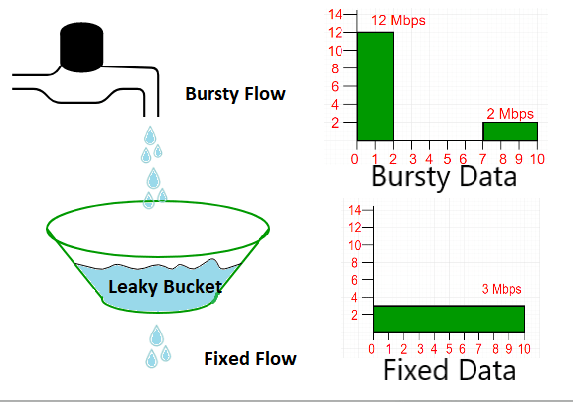






![1. A typical Bursty internet traffic network system [9] | Download Scientific Diagram 1. A typical Bursty internet traffic network system [9] | Download Scientific Diagram](https://www.researchgate.net/profile/Oyebayo-Olaniran/publication/318727778/figure/fig1/AS:631652921405465@1527609200355/A-typical-Bursty-internet-traffic-network-system-9.png)