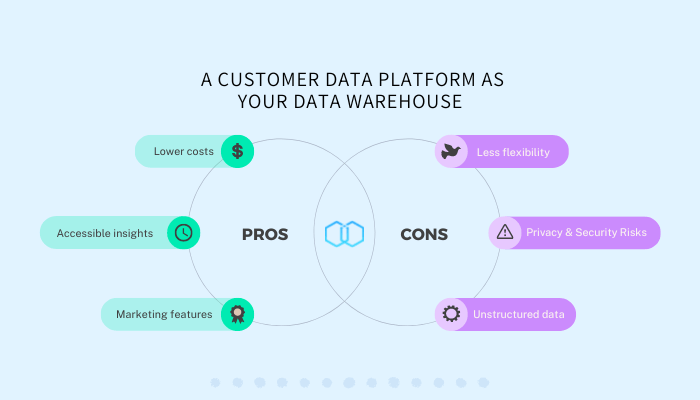
Data Warehouse Security Issues Ppt PowerPoint Presentation Inspiration Master Slide Cpb Pdf - PowerPoint Templates

Quantzig: Business Leaders Should Focus on Building a Modern Data Warehouse to Manage Critical Business Data | Business Wire

Extended Role Based Access Control – Based Design and Implementation for a Secure Data Warehouse Dr. Bhavani Thuraisingham Srinivasan Iyer. - ppt download