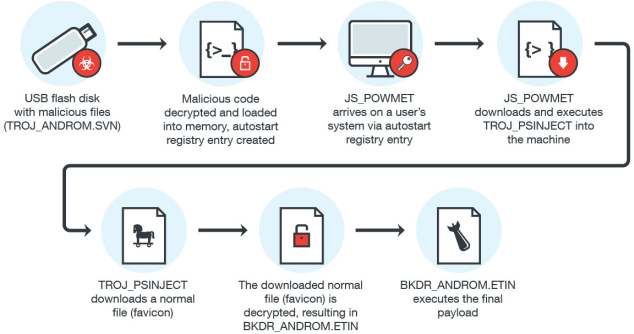
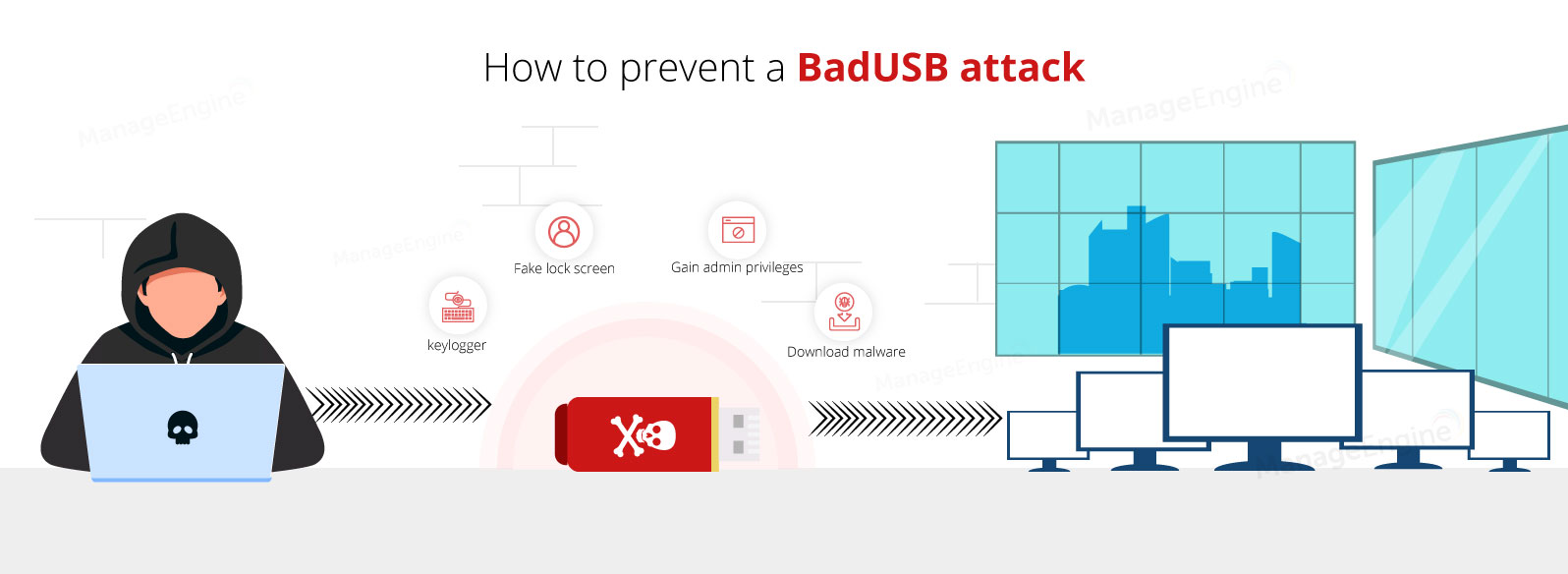
attacks - What are the risks and effects of the feared "Killer USB stick"? - Information Security Stack Exchange

USB Continue to Threat Critical Infrastructure Security: 29 Ways to Attack Production Facility by USB

Kitsap Networking Services, Inc. - USB DROP ATTACK, what do you need to know? There has been numerous threats and hacks that have been conducted in weird and new ways, but what